Some Topics That You Might Want To Pursue On Your Own That We Did Not Cover In This Article Are Listed Here The Work Described In This Article Is Mainly Focused On The Field Of “CISCO - Create VLAN Step By Step Configuration Example”. FOR MORE REFERENCE:
1. ◙ - ➤ Ethernet Switching:
2. ◙ - ➤ Ethernet Technical Overview:
3. ◙ - ➤ VLAN Trunking Protocol (VTP):
4. ◙ - ➤ VLAN Trunks With IEEE 802.1q:
5. ◙ - ➤ VLAN Trunks With Inter Switch Link (ISL):
6. ◙ - ➤ Native VLAN Configuration:
7. ◙ - ➤ Private VLANs (Rfc 5517) Configuration:
8. ◙ - ➤ ISL Vs IEEE 802.1q:
9. ◙ - ➤ VLAN Quick Reference:
10. ◙ - ➤ VLAN Notes:
11. ◙ - ➤ List Of Show Commands References (Routing & Switching):
12. ◙ - ➤ TSHOOT:
JUST RECAP ABOUT VLAN
VLAN A Network Is Divided Into Different Logical Segments Known As Broadcast Domains. The Computers In The VLAN Acts As They Are Connected With The Same LAN Segment Even They Are Located On The Different Network Segments. In The VLAN, Computers Can Move From One Location To Another And They Can Still Be The Part Of The Same VLAN.
◙ By Default, VLAN 1 Is The Native VLAN And Should Only Be Used To Carry Control Traffic, CDP, VTP, Pagp, And DTP. This Information Is Transmitted Across Trunk Links Untagged.
◙ User VLANs Should Not Include The Native VLAN, VLAN 1. This Information Will Be Sent As Tagged Frames Across VLAN Trunks.
◙ The Management VLAN Should Be A VLAN Separate From The User VLANs And Should Not Be The Native VLAN. This Will Insure Access To Networking Devices In Case Of Problems With The Network.
◙ The SUBINTERFACE On The Router That Is Used To Send And Receive Native VLAN Traffic Must Be Configured With The Native Option On The Encapsulation Interface Command. This Will Let The Router Know That Any Frames Coming In Untagged Belong To That Subinterface And Are A Member Of VLAN 1, The Native VLAN. This Is Assuming That The Native VLAN Is The VLAN 1, The Default Native VLAN.
SUMMARY OF VLAN:
✓ A VLAN Is A Broadcast Domain Formed By Switches.
✓ Administrators Must Create The VLAN’s Then Assign What Port Goes In What VLAN, Manually.
✓ VLAN’s Provide Better Performance For Medium And Large LAN’s.
✓ All Devices, By Default, Are In VLAN 1.
✓ A Trunk Port Is A Special Port That Runs ISL Or 802.1q So That It Can Carry Traffic From More Than One VLAN.
✓ For Devices In Different VLAN’s To Communicate, You Must Use A Router Or Layer 3 Switch. Because A Router Is Required For Inter-VLAN Communications, It Is Not Possible For Nonroutable Protocols To Communicate Outside Of Their VLANs.
✓ Dynamic VLAN: VLAN Membership Depends On The MAC Address Of The Workstation.
✓ Static VLAN: VLAN Membership Depends On The Switch Port To Which The Workstation Is Connected.
✓ Each VLAN Forms: Its Own Broadcast Domain. Each VLAN Is A Separate Subnet And Needs Its Own Subnet Address. The Switch Keeps A Separate Bridging Table For Each VLAN.
VLAN MEMBERSHIP DEPENDS ON THE SWITCH PORT TO WHICH THE WORKSTATION IS CONNECTED:
For Static VLAN; VLAN Membership Depends On The Switch Port To Which The Workstation Is Connected.
But For Dynamic VLAN; VLAN Membership Depends On The MAC Address Of The Workstation.
FOUR WAYS IN WHICH COMPUTERS ATTACHED TO A VLAN CAN BE ASSIGNED TO SPECIFIC VLANS INSIDE THEM:
1. Port-based VLANs (layer-1 VLANs)
2. MAC-based VLANs (layer-2 VLANs)
3. IP-based VLANs (layer-3 VLANS)
4. Application-based VLANs (layer-4 or policy-based VLANS)
◙ - ➤ For More Reference About VLAN Membership:
VLAN - BENEFITS AND LIMITATIONS
◙ SECURITY: Groups That Have Sensitive Data Are Separated From The Rest Of The Network, Decreasing The Chances Of Confidential Information Breaches.
◙ COST REDUCTION: Cost Savings Result From Less Need For Expensive Network Upgrades And More Efficient Use Of Existing Bandwidth And Uplinks. Some Of The Savings Are Reduced By Administrative Costs Needed For IT Staff To Configure Vlans Into Switches.
◙ HIGHER PERFORMANCE: Dividing Flat Layer 2 Networks Into Multiple Logical Workgroups (Broadcast Domains) Reduces Overall Network Utilization And Boosts Performance.
◙ BROADCAST STORM MITIGATION: Dividing A Network Into Smaller Logical Networks Results In Lower Susceptibility To Broadcast Storms.
◙ SIMPLER PROJECT OR APPLICATION MANAGEMENT: Vlans Bring Together All Required Players In A Way That Makes Managing A Project Or Working With A Specialized Application Easier.
◙ IMPROVED IT STAFF EFFICIENCY: Moves, Adds, And Changes Are Easier And Less Expensive To Perform. Network Administrators' Time Is Freed Up For Proactive Network Management.
VLAN LIMITATIONS:
◙ DEVICE LIMITATIONS: The Number Of Ethernet Addresses Than Can Be Supported By Each Device Is 500. This Is A Distribution Of About 20 Devices Per Port On A 25 Port Switch. In An Ideal Network Situation, There Is One Device Per Port, For Example, A Printer, A Workstation, And Voice IP Phone Will Require 3 Ports. If You Wanted To Have One VLAN Assignment For Each Port, Then The Maximum Vlans Will Equal 25.
◙ PORT CONSTRAINTS If A Hub Or Switch Is Connected To One Port, Every Port On That Hub Must Belong To The Same VLAN. Hubs Do Not Have The Capability To Provide Vlans To Individual Ports, And Vlans Can Not Be Extended Beyond The Device Port Even If A Switch Capable Of Supporting Vlans Is Attached.
TRUNK PORT ON A CISCO SWITCH
A Trunk Is A Point-To-Point Link Between The Device And Another Networking Device. Trunks Carry The Traffic Of Multiple VLANs Over A Single Link And Allow You To Extend VLANS Across An Entire Network.
To Correctly Deliver The Traffic On A Trunk Port With Several VLANs, The Device Uses The IEEE 802.1Q Encapsulation (Tagging) Method That Uses A Tag That Is Inserted Into The Frame Header. This Tag Carries Information About The Specific VLAN To Which The Frame And Packet Belong.
This Method Allows Packets That Are Encapsulated For Several Different VLANs To Traverse The Same Port And Maintain Traffic Separation Between The VLANs. The Encapsulated VLAN Tag Also Allows The Trunk To Move Traffic End-To-End Through The Network On The Same VLAN.
Once VLANS Have Been Defined On A Switch And You Have Placed Ports Into Their Corresponding VLANS, Traffic Is Limited To Remain Inside It’s Virtual LAN. The Only Way For Traffic To Leave The Switch, Is To Have It Sent On A Port That Is In The Same VLAN As Its Source, Or Sent Over A Trunk Port.
A Trunk Port Is A Port That Has Been Configured To Send And Receive Traffic From ANY And ALL VLANS. In Order To Send Traffic Over A Trunk Port, The Original Information About The VLAN Needs To Be Maintained. Since Multiple VLANS Will Be Sent Over A Single Cable / Port, The Next Switch Or Router Would Not Be Able To Identify Which VLAN It Needs To Belong To Without Some Type Of Identification Process.
THERE ARE CURRENTLY 2 SUPPORTED METHODS ON CISCO SWITCHES AND ROUTERS FOR MAINTAINING THE VLAN INFORMATION OVER A TRUNK.
◙ IEEE 802.1Q – Otherwise known as ‘Dot1q’
◙ ISL – Inter-Switch Link (Cisco Proprietary Protocol
FOR MORE REFERENCE:
◙ - ➤ VLAN Trunking Protocol (VTP):
◙ - ➤ VLAN Trunks With IEEE 802.1q:
◙ - ➤ VLAN Trunks With Inter Switch Link (ISL):
VLAN TAGGING
Moving VLAN Data Over Multiple Switches Uses A Method Called VLAN Tagging. The Act Of VLAN Tagging Simply Adds Extra Information In The Packet Header Of Ethernet Frames So Routers Know How To Pass Along The Data.
◙ VLAN Tagging Is Used When A Link Needs To Carry Traffic For More Than One VLAN.
TRUNK LINK: As Packets Are Received By The Switch From Any Attached End-Station Device, A Unique Packet Identifier Is Added Within Each Header.
◙ This Header Information Designates The VLAN Membership Of Each Packet.
◙ The Packet Is Then Forwarded To The Appropriate Switches Or Routers Based On The VLAN Identifier And MAC Address.
◙ Upon Reaching The Destination Node (Switch) The VLAN ID Is Removed From The Packet By The Adjacent Switch And Forwarded To The Attached Device.
◙ Packet Tagging Provides A Mechanism For Controlling The Flow Of Broadcasts And Applications While Not Interfering With The Network And Applications.
◙ This Is Known As A Trunk Link Or VLAN Trunking.
◙ VLAN Tagging Is Used When A Link Needs To Carry Traffic For More Than One VLAN.
◙ Tagging Is Used So The Receiving Switch Knows Which Ports In Should Flood Broadcast And Unknown Unicast Traffic (Only Those Ports Belonging To The Same VLAN).
ISL VS IEEE 802.1Q:
THERE ARE TWO MAJOR METHODS OF FRAME TAGGING:
◙ Cisco Proprietary Inter-Switch Link (ISL).
◙ And IEEE 802.1Q:
◙ ISL Used To Be The Most Common, But Is Now Being Replaced By 802.1Q Frame Tagging. ISL Increases The Frame Header Overhead By 30 Bytes.
◙ Cisco Recommends Using 802.1Q. This Type Of Encapsulation Adds Only 4 Bytes To The Ethernet Header
◙ - ➤ For More Reference About ISL Vs IEEE 802.1q:
VLAN TRUNK PROTOCOL (VTP)
Just Imagine, You Are Working In A Medium Company In A Multiple Floors Office. You Assigned Each Floor To A Switch For Easy Management And Of Course They Can Be Assigned To Different VLANs.
One Day, Your Boss Decides To Add A New Department To Your Office, The Support Department, And You Are Tasked To Add A New SUPPORT VLAN For This Department. How Will You Do That? Well, Without VTP You Have To Go To Each Switch To Enable This New VLAN (If VTP Is Not Running On These Switches). Fortunately Your Office Only Has 5 Floors So You Can Finish This Task In Whiten One Hours!
But If Your Company Was Bigger With 100-Floor Office And Some VLANs Needed To Be Added Every Month! Well, It Will Surely Become A Daunting Task To Add A New VLAN Like This. Luckily, Cisco Always “Thinks Big” To Create A Method For You To Just Sit At The “Main Switch”, Adding Your New VLANs And Magically, Other Switches Automatically Learn About This VLAN, It Is What VTP Does For You!
SUMMARY OF VTP:
◙ VTP Is A Cisco Proprietary Protocol That Allows VLAN Configuration To Be Consistently Maintained Across A Common Administrative Domain.
◙ VTP Minimizes The Possible Configuration Inconsistencies That Arise When Changes Are Made.
◙ Additionally, VTP Reduces The Complexity Of Managing And Monitoring VLAN Networks, Allowing Changes On One Switch To Be Propagated To Other Switches Via VTP.
◙ On Most Cisco Switches, VTP Is Running And Has Certain Defaults Already Configured.
VTP OPERATION:
◙ A Critical Parameter Governing VTP Function Is The VTP Configuration Revision Number.
◙ This 32-Bit Number Indicates The Particular Revision Of A VTP Configuration.
◙ A Configuration Revision Number Starts At 0 And Increments By 1 With Each Modification Until It Reaches 4294927295, At Which Point It Recycles Back To 0 And Starts Incrementing Again.
◙ Each VTP Device Tracks Its Own VTP Configuration Revision Number.
◙ VTP Packets Contain The Sender’s VTP Configuration Number.
◙ This Information Determines Whether The Received Information Is More Recent Than The Current Version.
◙ If The Switch Receives A VTP Advertisement Over A Trunk Link, It Inherits The VTP Domain Name And Configuration Revision Number.
◙ The Switch Ignores Advertisements That Have A Different VTP Domain Name Or An Earlier Configuration Revision Number.
IT HAS THREE VTP OPERATION MODE:
✓ VTP Server Mode,
✓ VTP Client Mode.
✓ VTP Transparent Mode,
◙ - ➤ VTP SERVER MODE: The Default Mode. When You Make A Change To The VLAN Configuration On A VTP Server, The Change Is Propagated To All Switches In The VTP Domain. VTP Messages Are Transmitted Out Of All The Trunk Connections. In Server Mode We Can Create, Modify, Delete VLANs.
◙ - ➤ VTP CLIENT MODE: Cannot Make Changes To The VLAN Configuration When In This Mode; However, A VTP Client Can Send Any VLANs Currently Listed In Its Database To Other VTP Switches. VTP Client Also Forwards VTP Advertisements (But Cannot Create VTP Advertisements).
VTP Clients Cannot Create, Modify, Or Delete VLAN Information. The Only Role Of VTP Clients Is To Process VLAN Changes And Send VTP Messages Out All Trunk Ports. The VTP Client Maintains A Full List Of All VLANs Within The VTP Domain, But It Does Not Store The Information In NVRAM.
VTP Clients Behave The Same Way As VTP Servers, But It Is Not Possible To Create, Change, Or Delete VLANs On A VTP Client. VTP Server Advertisement. By VTP Client
◙ - ➤ VTP TRANSPARENT MODE: When You Make A Change To The VLAN Configuration In This Mode, The Change Affects Only The Local Switch And Does Not Propagate To Other Switches In The VTP Domain. VTP Transparent Mode Does Forward VTP Advertisements That It Receives Within The Domain.
Switches In VTP Transparent Mode Forward VTP Advertisements But Ignore Information Contained In The Message. A Transparent Switch Will Not Modify Its Database When Updates Are Received, Nor Will The Switch Send Out An Update Indicating A Change In Its Own VLAN Status.
Except For Forwarding VTP Advertisements, VTP Is Disabled On A Transparent Switch. There Is Also An “Off” VTP Mode In Which Switches Behave The Same As In The VTP Transparent Mode, Except VTP Advertisements Are Not Forwarded.
HOW VTP WORKS:
To Make Switches Exchange Their VLAN Information With Each Other, They Need To Be Configured In The Same VTP Domain. Only Switches Belonging To The Same Domain Share Their VLAN Information. When A Change Is Made To The VLAN Database, It Is Propagated To All Switches Via VTP Advertisements.
✓ To Maintain Domain Consistency, Only One Switch Should Be Allowed To Create (Or Delete, Modify) New VLAN. This Switch Is Like The “Master” Of The Whole VTP Domain And It Is Operated In Server Mode. This Is Also The Default Mode.
✓ Other Switches Are Only Allowed To Receive And Forward Updates From The “Server” Switch. They Are Operated In Client Mode.
✓ In Some Cases, The Network Manager Doesn’t Want A Switch To Learn VTP Information From Other Switches. He Can Set It To Transparent Mode. In This Mode, A Switch Maintains Its Own VLAN Database And Never Learn VTP Information From Other Switches (Even The Server). However, It Still Forwards VTP Advertisements From The Server To Other Switches (But Doesn’t Read That Update). A Transparent Switch Can Add, Delete And Modify VLAN Database Locally.
SWITCHES AS THE “SERVER MODE”: VTP Advertisements Bring VLAN Information To All The Switches In A VTP Domain. Each VTP Advertisement Is Sent With A Revision Number. This Number Is Used In Order To Determine Whether The VTP Advertisement Is More Recent Than The Current Version Of That Switch. Because Each Time You Make A VLAN Change In A Switch, The Configuration Revision Is Incremented By One. So The Higher The Revision Number, The Better Your VTP Advertisement.
For Example, The First Time The Main Switch Sends A VTP Advertisement, Its Revision Number Is 1. When You Add A New VLAN To The Main Switch, It Will Send A VTP Advertisement With The Revision Number Of 2. Client Switches First Receive The VTP Advertisement With The Revision Number Of 1, Which Is Bigger Than Its Current Revision Number (0) So It Updates Its VLAN Database. Next It Receives The VTP Advertisement With The Revision Number Of 2, It Continues Comparing With Its Current Revision Number (1) -> It Continues Update Its VLAN Database.
One Important Thing You Must Know Is When A Switch Receives A Better VTP Advertisement, It Deletes Its Whole VTP Information And Copy The New Information From The Better VTP Advertisement To Its VLAN Database. A Switch Does Not Try To Compare Its Own VLAN Database With Information From The Received VTP Advertisements To Find Out And Update The Difference!
Note: VTP Advertisements Are Sent As Multicast Frames And All Neighbors In That Domain Receive The Frames.
The Switch Supports VLANs In VTP Client, Server, And Transparent Modes. VLANs Are Identified By A Number From 1 To 4094. VLAN IDs 1002 Through 1005 Are Reserved For Token Ring And FDDI VLANs.
VTP Only Learns Normal-Range VLANs, With VLAN IDs 1 To 1005; VLAN IDs Greater Than 1005 Are Extended-Range VLANs And Are Not Stored In The VLAN Database. The Switch Must Be In VTP Transparent Mode When You Create VLAN IDs From 1006 To 4094.
Although The Switch Supports A Total Of 255 (Normal Range And Extended Range) VLANs, The Number Of Configured Features Affects The Use Of The Switch Hardware. The Switch Also Supports Per-VLAN Spanning-Tree Plus (PVST+) Or Rapid PVST+ With A Maximum Of 128 Spanning-Tree Instances. One Spanning-Tree Instance Is Allowed Per VLAN.
◙ - ➤ For More Reference About VLAN Trunking Protocol (VTP):
VTP CONFIGURATION STEPS
◙ VTP Can Be Configured By Using These Configuration Modes.
- VTP Configuration In Global Configuration Mode
- VTP Configuration In VLAN Configuration Mode
◙ VLAN Configuration Mode Is Accessed By Entering The VLAN Database Privileged EXEC Command.
◙ Two Different Versions Of VTP Can Run In The Management Domain, VTP Version 1 And VTP Version 2.
◙ The Two Versions Are Not Interoperable In The Same VTP Domain.
◙ The Major Difference Between The Two Versions Is Version 2 Introduces Support For Token Ring VLANS.
◙ If All Switches In A VTP Domain Can Run VTP Version 2, Version 2 Only Needs To Be Enabled On One VTP Server Switch, Which Propagates It To Other VTP Switches In The VTP Domain.
◙ Version 2 Should Not Be Enabled Unless Every Switch In The VTP Domain Supports Version 2.
◙ The Domain Name Can Be Between 1 And 32 Characters.
◙ The Optional Password Must Be Between 8 And 64 Characters Long.
◙ If The Switch Being Installed Is The First Switch In The Network, The Management Domain Will Need To Be Created.
◙ However, If The Network Has Other Switches Running VTP, Then The New Switch Will Join An Existing Management Domain.
◙ Caution: The Domain Name And Password Are Case Sensitive.
◙ By Default, Management Domains Are Set To A Nonsecure Mode, Meaning That The Switches Interact Without Using A Password.
◙ Adding A Password Automatically Sets The Management Domain To Secure Mode.
◙ The Same Password Must Be Configured On Every Switch In The Management Domain To Use Secure Mode.
VTP CONFIGURATION ON VTP MODE:
CONFIGURATION ON VTP MODE AS A CLIENT/SERVER/TRANSPARENT:
Switch#Config Terminal
Switch(config)#VTP mode [Client|Server|Transparent]
Switch#VLAN Database
Switch(VLAN)#VTP [Client|Server|Transparent]
VTP CONFIGURATION IN GLOBAL CONFIGURATION MODE:
Switch#config Terminal
Switch(config)#VTP Version 2
Switch(config)#VTP Mode server
Switch(config)#VTP Domain cisco
Switch(config)#VTP Password mypassword
VTP CONFIGURATION IN VLAN CONFIGURATION MODE:
Switch#VLAN Database
Switch(vlan)#VTP v2-mode
Switch(vlan)#VTP Server
Switch(vlan)#VTP Domain cisco
Switch(vlan)#VTP Password mypassword
VERIFYING VTP:
✓ The Most Important Command To View The Status Of VTP On Cisco Switches. Command Is ”SHOW VTP STATUS” – > Displays The VTP Statistics And Domain Information
✓ This Command Is Used To Display Statistics About Advertisements Sent And Received On The Switch. ”SHOW VTP COUNTERS”
VTP PRUNING:
◙ To Stop Unwanted Traffic.
◙ Block The VTP Advertisements.
◙ By Default VTP Pruning Is Disable.
◙ VTP Pruning Makes More Efficient Use Of Trunk Bandwidth By Forwarding Broadcast And Unknown Unicast Frames On A VLAN Only If The Switch On The Receiving End Of The Trunk Has Ports In That VLAN.
TO ENABLE VTP PRUNING:
Switch(config)# VTP Pruning
Note: By Default VTP Pruning Is Disable. VTP Pruning Work on The VTP Receive Advertisement It’ll Send The Packet to the Same VLAN Only.
◙ To Check: “Show VTP Status” Command And #Show Interface Trunk Are Use. This Commands Will Help To Display VTP Enable.
INTER-VLAN ROUTING:
VLAN (Virtual Local Network) is a logically separate IP subnetwork which allow multiple IP networks and subnets to exist on the same-switched network. VLAN is a logical broadcast domain that can span multiple physical LAN segments. VLANs Divide Broadcast Domains In A LAN Environment, Switches Operate At Layer2 (Data link Layer).
By Default VLANS Cannot Communicate Without L3 (Network Layer), Whenever Hosts In One VLAN Need To Communicate With Hosts In Another VLAN, The Traffic Must Be Routed Between Them. This Is Known As Inter-VLAN Routing. VLANs Are Also Subnets. A Subnet, Or A Network, Is A Contained Broadcast Domain. A Broadcast That Occurs In One Subnet Will Not Be Forwarded, By Default, To Another Subnet. Routers, Or Layer-3 Devices, Provide This Boundary Function. Switch Provide This Function At Layer 2 By VLAN.
Inter-VLAN Routing As A Process Of Forwarding Network Traffic From One VLAN To Another VLAN Using A Router Or Layer 3 Device. As We Know That Each VLAN Is A Unique Broadcast Domain, So, Computers On Separate VLANs Are, By Default, Not Able To Communicate. There Is A Way To Permit These Computers To Communicate; It Is Called Inter-VLAN Routing. One Of The Ways Of The Ways To Carry Out Inter-VLAN Routing Is By Connecting A Router To The Switch Infrastructure.
Inter-VLAN Routing Is A Process Of Forwarding Network Traffic From One VLAN To Another Using A Router The Subnets Of Your Network Facilitate The Routing Process. On A Router We Configure The IP Address On The Physical Interface, However On A Switch The Physical Interfaces Are Running At Layer 2.
To Connect To The Switch Via “Telnet Or SSH” You Need To Have A Management IP Address Configured. Similarly, If You Are Connecting To The Switch From A Different Subnet, The Switch Will Require A Default-Gateway In Order To Have The Packets Routed Back To You.
◙ We Define Inter-VLAN Routing As A Process Of Forwarding Traffic From One VLAN To Another VLAN Using A Router.
◙ VLANs Are Associated With Unique IP Subnets On The Network.
◙ When Using A Router To Facilitate Inter-VLAN Routing, The Router Interfaces Can Be Connected To Separate VLANs.
◙ Devices On Those VLANs Send Traffic Through The Router To Reach Other VLANs.
WHAT IS DEFAULT ROUTE?
Default Gateway A Gateway Is A Node On A TCP/IP Network That Serves As An Access Point To Another Network. Is The Device That Passes Traffic From The Local Subnet To Devices On Other Subnets. Default Routes To Direct Packets Addressed To Destinations Or Networks Not Found Or Listed In The Routing Table. This Is More Workable In A Stub Network (Networks With One Exit Path). To Configure A Default Route, You Will Use Wildcards In The Network Address And Mask. Using Default Route Helps To Reduce The Complex Work Of Configuring All The Assigned Routes.
When You As The Network Administrator Create A Static Route To Network 0.0.0.0 0.0.0.0 This Is Another Way Of Setting The Gateway Of Last Resort On A Router.However, IP Routing Must Be Enabled On The Router, If Not; It’s Advisable To Use The IP Default Gateway Command.
Note: When VLAN Information To Communicate From One Switch To Another Within The Same VLAN We Need To Configure The Link Port Between Switches As Trunk Ports. Use “Switchport Mode Trunk”Command.
And To Enable Connectivity Between Two Different VLAN We Need To Add A Layer 3 Device And Configure INTERVLAN ROUTING On It.
WHAT IS VLAN SUBINTERFACES?:
A Sub-Interface Is A Logical Interface That Uses The "Parent" Physical Interface For Actually Moving The Data.
◙ Subinterfaces Are Multiple Virtual Interfaces, Associated With One Physical Interface.
◙ Subinterfaces Allow A Router To Scale To Accommodate More VLANs Than The Physical Interfaces Permit.
◙ Subinterfaces Are Configured For Different Subnets Corresponding To Their VLAN Assignment To Facilitate Logical Routing Before The Data Frames Are VLAN Tagged And Sent Back Out The Physical Interface.
VTP CONFIGURATION EXAMPLE
Main Switch(Config)#VTP Version 2
Main Switch(Config)#VTP Domain SCN
Main Switch(Config)#VTP Mode Server
Main Switch(Config)#VTP Password Keepitsecret
VTP CONFIGURATION ON CLIENT SWITCHES:
Client Switch(Config)#VTP Version 2
Client Switch(Config)#VTP Domain SCN
Client Switch(Config)#VTP Password Keepitsecret
Client Switch(Config)#VTP Mode Client
Note: Before Configuring VTP Make Sure The Links Between Your Switches Are Trunk Links. Your Trunk Link Can Automatically Be Formed If Both Of Your Switches Are Not 2960 Or 3560 Because Ports On The 2960 And 3560 Switches Are Set To Dynamic Auto By Default. If Both Sides Are Set To Dynamic Auto, The Link Will Remain In Access Mode.
TO CONFIGURE TRUNK BETWEEN THESE PORTS, USE THESE COMMANDS:
Client(Config)#Interface Fa0/1 (Or The Interface On The Link You Want To Be Trunk)
Client(Config-If)#Switchport Mode Trunk (These Commands Only Need To Be Used On One Of Two Switches To Form The Trunk).
STEP BY STEP EXAMPLES FOR CREATE A VLAN:
1. Create Vlans
2. Assign Ports To Vlans
3. Verify Vlan Config
4. Enable Trunking On Inter-Switch & Switch Router Links
5. Verify Trunk Configs
VERIFYING VLAN (Always Remember These Commands):
SWITCH1#Show IP Routing
SWITCH1#Show Flash
SWITCH1#Show IP Interface Brief
SWITCH1#Show Interface Fa0/3 Switchport
SWITCH1#Show CDP Neighbor
SWITCH1#Show CDP 30.0.0.2
SWITCH1#Debug CDP Packet
SWITCH1#Show Interfaces Trunk
SWITCH1#Show Vlan
SWITCH1#Show Vlan Brief
SWITCH1##Show Vlan Name
SWITCH1#Show Vlan Summary
SWITCH1#Show Interfaces Vlan #
SWITCH1#Show Interfaces X/X
SWITCH1#Show VTP Status
SWITCH1#Show MAC–Address-Table
SHOW VLAN – > Displays VLAN Memberships On A Switch
SHOW INTERFACE TRUNK – > Displays Port And Module Interface Trunk Information
SHOW MAC-ADDRESS-TABLE – > Displays The Forward/Filter (Mac Address) Table
SHOW VTP STATUS – > Displays The VTP Statistics And Domain Information
SHOW CDP NEIGHBORS - > Cisco Discovery Protocol (CDP) Command Shows Directly Connect Cisco Device Information Including Hostname, Local And Remote Port(S), Device Capabilities And Platform.
◙ - ➤ List Of Show Commands References:
CONFIGURATION EXAMPLE FOR CREATE VLAN:
◙ - ➤ CONFIGURATION TO CREATE VLAN 2 AND 3 ON “SWITCH A” (VTP SERVER):
✓ To Create A VLAN, First Enter Global Configuration Mode To Run The Following Commands.
Switch A(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch A(Config)#VLAN 2 (Defining The VLAN 2)
Switch A(Config)#VLAN 2 Name Marketing (Assigning The Name Marketing To VLAN 2)
Switch A(Config)#VLAN 3 (Defining The VLAN 3)
Switch A(Config)#VLAN 3 Name Management (Assigning The Name Management To VLAN 3)
Switch A(Config)#Exit (Exit From VLAN 3)
◙ - ➤ ENTER THE FOLLOWING COMMANDS TO ADD PORT 2 AND 3 TO VLAN 2:
✓ Now Assigning The Ports 2 And 3 To VLAN 2, It Must Be Done From The Interface Mode.
Switch A(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch A(Config)#Interface Fastethernet 0/2 (Select The Ethernet 0 Of Port 2)
Switch A(Config-If)#Switchport Access VLAN 2 (Allot The Membership Of VLAN 2)
Switch A(Config-If)#Exit (Exit From Interface 2)
Switch A(Config)#Interface Fastethernet 0/3 (Select The Ethernet 0 Of Port 3)
Switch A(Config-If)#Switchport Access Vlan 2 (Allot The Membership Of VLAN 2)
Switch A(Config-If)#Exit (Exit From Interface 3)
◙ - ➤ NOW ASSIGNING THE PORTS 4 AND 5 TO VLAN 3, ENTER THE FOLLOWING COMMANDS TO ADD PORT 4 AND 5 TO VLAN 3:
Switch A(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch A(Config)#Interface Fastethernet 0/4 (Select The Ethernet 0 Of Port 4)
Switch A(Config-If)#Switchport Access Vlan 3 (Allot The Membership Of Vlan 3)
Switch A(Config-If)#Exit (Exit From Interface 4)
Switch A(Config)#Interface Fastethernet 0/5 (Select The Ethernet 0 Of Port 5)
Switch A(Config-If)#Switchport Access Vlan 3 (Allot The Membership Of Vlan 3)
Switch A(Config-If)#Exit (Exit From Interface 5)
◙ - ➤ CONFIGURATION OF VTP CLIENT ON “SWITCH B”:
Switch B#VLAN Database
Switch B(Vlan)#VTP Client
Switch B(Vlan)#VTP Domain Group1
Switch B(Vlan)#Exit
◙ - ➤ NOW CREATE 802.1Q TRUNK LINK BETWEEN THE TWO SWITCHES TO ALLOW COMMUNICATION BETWEEN VLANS.
✓ TRUNKING WITH 802.1Q On Both Switches, “SWITCH A” AND “SWITCH B” Type The Following Command With 802.1q At The Fastethernet 0/1 Interface.
◙ CREATE 802.1Q TRUNK LINK ON SWITCH A:
Switch A(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch A(Config)#Interface Fastethernet 0/1 (Select The Ethernet 0 Of Port 1)
Switch A(Config-If)#Switchport Mode Trunk (Set Port 1 As Trunk Port)
Switch A(Config-If)#Switchport Trunk Encapsulation Dot1q
Switch A(Config-If)#End (Exit From Interface 1)
◙ CREATE 802.1Q TRUNK LINK ON SWITCH B:
Switch B(Config)#Interface Fastethernet 0/1 (Select The Ethernet 0 Of Port 1)
Switch B(Config-If)#Switchport Mode Trunk (Set Port 1 As Trunk Port)
Switch B(Config-If)#Switchport Trunk Encapsulation Dot1q
SwitchB(Config-If)#End (Exit From Interface 1)
✓ To Verify That Fastethernet 0/1 Has Been Established As Trunk Port, Type The Show Interface Fastethernet 0/1 Switchport At The Privileged Exec Mode.
✓ Although The VLAN Definitions Have Migrated To The Switch B Using VTP, But It Is Necessary To Assign Ports To These VLANS On Switch B.
✓ Now Assigning The Ports 2 And 3 To VLAN 2,It Must Be Done From The Interface Mode.
◙ - ➤ ENTER THE FOLLOWING COMMANDS TO ADD PORT 2 AND 3 TO VLAN 2:
Switch B(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch B(Config)#Interface Fastethernet 0/2 (Select The Ethernet 0 Of Port 2)
Switch B(Config-If)#Switchport Access Vlan 2 (Allot The Membership Of Vlan 2)
Switch B(Config-If)#Exit (Exit From Interface 2)
Switch B(Config)#Interface Fastethernet 0/3 (Select The Ethernet 0 Of Port 3)
Switch B(Config-If)#Switchport Access Vlan 2 (Allot The Membership Of Vlan 2)
Switch B(Config-If)#Exit (Exit From Interface 3)
◙ - ➤ NOW ASSIGNING THE PORTS 4 AND 5 TO VLAN 3, ENTER THE FOLLOWING COMMANDS TO ADD PORT 4 AND 5 TO VLAN 3
Switch B(Config)#Configure Terminal (Enter In Global Configuration Mode)
Switch B(Config)#Interface Fastethernet 0/4 (Select The Ethernet 0 Of Port 4)
Switch B(Config-If)#Switchport Access Vlan 3 (Allot The Membership Of Vlan 3)
Switch B(Config-If)#Exit (Exit From Interface 4)
Switch B(Config)#Interface Fastethernet 0/5 (Select The Ethernet 0 Of Port 5)
Switch B(Config-If)#Switchport Access Vlan 3 (Allot The Membership Of Vlan 3)
Switch B (Config-If)#Exit (Exit From Interface 5)
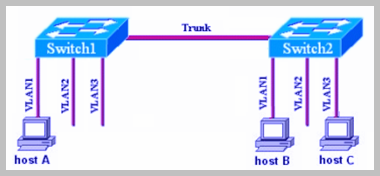
VLAN EXAMPLE - 001
We Have Three VLANs. VLAN 2,3, and 4. VLAN 4 Belongs Both To SWITCH 1 And SWITCH 2, Therefore We Need A Trunk Port Between The Two Switches In Order For Hosts In VLAN4 In Switch 1 To Be Able To Communicate With Hosts In VLAN4 In Switch 2.
THE PORTS OF THE TWO SWITCHES SHALL BE CONFIGURED AS FOLLOWING:
◙ - ➤ SWITCH 1:
Fe0/1 – Fe0/2 –> VLAN 2 (Accounting)
Fe0/10 – Fe0/11 –> VLAN 4 (Engineering)
Fe0/24 –> Trunk Port
◙ - ➤ SWITCH 2:
Fe0/1 – Fe0/2 –> VLAN 3 (Management)
Fe0/10 – Fe0/11 –> VLAN 4 (Engineering)
Fe0/24 –> Trunk Port
CONFIGURATION:
◙ - ➤ CONFIGURATION ON SWITCH 1:
Create VLANs 2 and 4 in the switch database:
Switch1# Configure Terminal
Switch1(Config)# Vlan 2
Switch1(Config-Vlan)# Name Accounting
Switch1(Config-Vlan)# End
Switch1(Config)# Vlan 4
Switch1(Config-Vlan)# Name Engineering
Switch1(Config-Vlan)# End
Assign Ports Fe0/1 and Fe0/2 in VLAN 2:
Switch1(Config)# Interface Fastethernet0/1
Switch1(Config-If)# Switchport Mode Access
Switch1(Config-If)# Switchport Access Vlan 2
Switch1(Config-If)# End
Switch1(Config)# Interface Fastethernet0/2
Switch1(Config-If)# Switchport Mode Access
Switch1(Config-If)# Switchport Access Vlan 2
Switch1(Config-If)# End
Assign Ports Fe0/10 and Fe0/11 in VLAN 4:
Switch1(config)# interface fastethernet0/10
Switch1(config-if)# switchport mode access
Switch1(config-if)# switchport access vlan 4
Switch1(config-if)# end
Switch1(config)# interface fastethernet0/11
Switch1(config-if)# switchport mode access
Switch1(config-if)# switchport access vlan 4
Switch1(config-if)# end
Create Trunk Port Fe0/24:
Switch1(Config)# Interface Fastethernet0/24
Switch1(Config-If)# Switchport Mode Trunk
Switch1(Config-If)# Switchport Trunk Encapsulation Dot1q
Switch1(Config-If)# End
◙ - ➤ CONFIGURATION ON SWITCH 2:
Create VLANs 3 and 4 in the switch database
Switch2# Configure Terminal
Switch2(Config)# Vlan 3
Switch2(Config-Vlan)# Name Management
Switch2(Config-Vlan)# End
Switch2(Config)# Vlan 4
Switch2(Config-Vlan)# Name Engineering
Switch2(Config-Vlan)# End
Assign Ports Fe0/1 and Fe0/2 in VLAN 3:
Switch2(Config)# Interface Fastethernet0/1
Switch2(Config-If)# Switchport Mode Access
Switch2(Config-If)# Switchport Access Vlan 3
Switch2(Config-If)# End
Switch2(Config)# Interface Fastethernet0/2
Switch2(Config-If)# Switchport Mode Access
Switch2(Config-If)# Switchport Access Vlan 3
Switch2(Config-If)# End
Assign Ports Fe0/10 and Fe0/11 in VLAN 4:
Switch2(Config)# Interface Fastethernet0/10
Switch2(Config-If)# Switchport Mode Access
Switch2(Config-If)# Switchport Access Vlan 4
Switch2(Config-If)# End
Switch2(Config)# Interface Fastethernet0/11
Switch2(Config-If)# Switchport Mode Access
Switch2(Config-If)# Switchport Access Vlan 4
Switch2(Config-If)# End
Create Trunk Port Fe0/24:
Switch2(Config)# Interface Fastethernet0/24
Switch2(Config-If)# Switchport Mode Trunk
Switch2(Config-If)# Switchport Trunk Encapsulation Dot1q
Switch2(Config-If)# End
VLAN EXAMPLE - 002
All Ports Are Either In Access Mode Or Trunk Mode, The Access Mode Allows The Port To Communicate With The VLAN. The Trunk Mode Carries The VLAN Traffic To Another Switch (Or Device).
◙ - ➤ SWITCH01:
Switch01>Enable
Password: Xxxxxxxx
Switch01#Configure Terminal
Enter Configuration Commands, One Per Line. End With CNTL/Z.
Switch01(Config)#Vlan 10
Switch01(Config-Vlan)#Name Admin
Switch01(Config-Vlan)#Exit
Switch01(Config)#Vlan 20
Switch01(Config-Vlan)#Name Data
Switch01(Config-Vlan)#Exit
Switch01(Config)#Int F0/2
Switch01(Config-If)#Switchport Mode Access
Switch01(Config-If)#Switchport Access Vlan 10
Switch01(Config-If)#Exit
Switch01(Config)#Inf F0/16
Switch01(Config-If)#Switchport Mode Access
Switch01(Config-If)#Switchport Access Vlan 20
Switch01(Config-If)#Exit
Switch01(Config)#Int F0/23
Switch01(Config-If)#Switchport Mode Trunk
Switch02(Config-If)#Switchport Trunk Allowed Vlan 1,10,20
Switch01(Config-If)#Exit
Switch01(Config)#Exit
Switch01#Write Mem
Building Configuration...
Switch01#
◙ - ➤ SWITCH02:
Switch02>Enable
Password: Xxxxxxx
Switch02#Configure Terminal
Enter Configuration Commands, One Per Line. End With CNTL/Z.
Switch02(Config)#Vlan 10
Switch02(Config-Vlan)#Name Admin
Switch02(Config-Vlan)#Exit
Switch02(Config)#Vlan 20 Switch02(Config-Vlan)#Name Data
Switch02(Config-Vlan)#Exit
Switch02(Config)#Int F0/2
Switch02(Config-If)#Switchport Mode Access
Switch02(Config-If)#Switchport Access Vlan 10
Switch02(Config-If)#Exit
Switch02(Config)#Inf F0/15
Switch02(Config-If)#Switchport Mode Access
Switch02(Config-If)#Switchport Access Vlan 20
Switch02(Config-If)#Exit
Switch02(Config)#Int F0/1
Switch02(Config-If)#Switchport Mode Trunk
Switch02(Config-If)#Switchport Trunk Allowed Vlan 1,10,20
Switch02(Config-If)#Exit
Switch02(Config)#Exit
Switch02#Write Mem
Building Configuration...
Switch02#
VLAN QUEST
Answer: VTP Manages The Addition, Deletion, And Renaming Of VLANs From A Centralized Location.
2. HOW ARE NONROUTABLE PROTOCOLS AFFECTED BY VLANS?
Answer: Because A Router Is Required For Inter-VLAN Communications, It Is Not Possible For Nonroutable Protocols To Communicate Outside Of Their VLANs.
3. HOW DOES THE CATALYST 3550 SWITCH, WITH LAYER 3 SOFTWARE INSTALLED, DEAL WITH PACKETS THAT ARE FOR AN UNKNOWN DESTINATION?
Answer: If A Default Route Is Configured, Or You Are Using A Routing Protocol To Receive Routing Information, The 3550 Switch Can Send The Packet To The Default Gateway For Delivery; Otherwise, It Is Dropped.
4. WHY WOULD YOU CONFIGURE AN INTERFACE AS A TRUNK?
Answer: A Trunk Is An Interface That Is A Member Of All Vlans In The VLAN Database Unless You Specifically Prohibit Its Membership To Certain Vlans. This Is The Only Way That An Interface Can Be A Member Of Multiple Vlans And See The Traffic On Them.
5. WHY WOULD YOU SEE AN UNTAGGED PACKET ON A SWITCH THAT IS CONFIGURED WITH VLANS?
Answer: The Native VLAN, The One Configured On The Port, Does Not Need A Tag Because It Is Assumed That Any Packet Received On It Is For The Configured VLAN.
6. WHY WOULD YOU USE PAGP?
Answer: Port Aggregation Protocol (Pagp) Allows An Etherchannel To Be Formed Dynamically Without Having To Configure Both Sides Of The Channel.
7. WHAT IS A ROUTED PORT?
Answer: A Routed Port Is A Physical Port That Acts Like A Port On A Router Without Requiring You To Have A Router.
8. WHAT IS A DESIGNATED PORT?
Answer: A Designated Port Is An Elected Forwarding Port That Is Logically Closer To The Root Switch.
9. WHAT CAN PREVENT AN ALTERNATE OR ROOT PORT FROM BECOMING THE DESIGNATED PORT AFTER A UNIDIRECTIONAL LINK FAILURE?
Answer: The Loop Guard Feature Provides This Protection.
10. WHAT CAN PREVENT PACKETS WITH AN UNKNOWN DESTINATION MAC ADDRESS FROM BEING FLOODED TO EVERY PORT ON A SWITCH?
Answer: Port Blocking Can Provide This Protection For Unicast And Multicast Packets.
11. HOW MANY VLANS CAN BE CONFIGURED ON A CATALYST SWITCH?
a) 99
b) 255
c) 1024
d) 4096
Answer: b (255)
12. A SWITCH IS CONFIGURED WITH FOUR VLANS. WHICH IS TRUE?
a) Each VLAN Forms Its Own Broadcast Domain.
b) Each VLAN Is A Separate Subnet And Needs Its Own Subnet Address.
c) The Switch Keeps A Separate Bridging Table For Each VLAN.
d) All Of The Above.
Answer: d (a,b,c)
13.WHICH VLAN IS USED FOR STP AND CDP MESSAGES?
a) Vlan 1
b) The Management Vlan
c) The Native Vlan
d) The Data Vlan
e) Any Vlan You Choose
Answer: a
14. WHICH IS TRUE OF A STATIC VLAN?
a) VLAN Membership Depends On The MAC Address Of The Workstation.
b) VLAN Membership Depends On The IP Address Of The Workstation.
c) VLAN Membership Depends On The Switch Port To Which The Workstation Is Connected.
d) It Is Not Possible To Change The VLAN Membership Once It Has Been Configured.
e) Static Vlans Require The Use Of Special Software Packages Such As Ciscoworks 2000.
Answer: c
15. WHICH IS TRUE OF A DYNAMIC VLAN?
a) VLAN Membership Depends On The MAC Address Of The Workstation.
b) VLAN Membership Depends On The Switch Port To Which The Workstation Is Connected.
c) It Is Not Possible To Change The VLAN Membership Once It Has Been Configured.
d) Dynamic Vlans Have Become Common Since The Introduction Of DHCP.
Answer: a
16. YOU HAVE CONFIGURED STATIC VLANS ON A SWITCH. THE MARKETING DEPARTMENT USES VLAN 4. A MEMBER OF THE MARKETING DEPARTMENT MOVES TO A DIFFERENT OFFICE, TAKING HER PC WITH HER. WHAT NEEDS TO BE DONE?
a) Nothing. The PC Will Be Recognised In Its New Position And Will Stay On VLAN 4.
b) The Cabling Must Be Altered So That The PC Is Still Connected To One Of The Switch Ports On VLAN 4.
c) The Switch Configuration Must Be Altered So That The Port Connected To The PC Is Reassigned To VLAN 4.
d) The VLAN Must Be Changed To A Dynamic VLAN.
Answer: c
17. A SWITCH HAS STATIC VLANS CONFIGURED. THREE WORKSTATIONS ARE CONNECTED TO THE SAME SWITCH PORT BY USING A HUB. WHAT IS THE EFFECT OF THIS?
a) The Three Workstations Must Be On The Same VLAN.
b) The Hub Must Be Configured With The Same Static Vlans As The Switch.
c) The Switch Must Be Configured With Sub Interfaces If The Workstations Are On Different Vlans.
d) It Is Not Possible For Workstations To Share A Switch Port When Vlans Are Used.
Answer: a
18. THE MARKETING DEPARTMENT IS ON VLAN 4 AND THE SALES DEPARTMENT IS ON VLAN 5. HOW CAN A MEMBER OF THE MARKETING DEPARTMENT COMMUNICATE WITH A MEMBER OF THE SALES DEPARTMENT?
a) The Switch Will Detect That The Destination Is On A Different Segment And Flood Packets Through All Ports
b) The Switch Needs To Be Configured To Pass Packets Between Different Vlans.
c) The Packets Must Be Sent Via An Enterprise Server.
d) A Router Is Needed To Route Packets Between Different Vlans.
Answer: d
19. A NEW SWITCH HAS THE DEFAULT CONFIGURATION. WHICH OF THE FOLLOWING ARE TRUE? (CHOOSE TWO)
a) VLAN 1 Exists, And All Ethernet Ports Are Assigned To It.
b) Each Group Of Eight Ports Is Assigned To A Different VLAN.
c) An IP Address Is Assigned To VLAN 1.
d) There May Be Default Vlans For Different LAN Technologies, Such As Token Ring And FDDI.
Answer: a And d
20. An Administrator Wants To Configure An IP Address On A Switch So That The Switch Can Be Configured Remotely. What Should The Administrator Do?
a) Configure The IP Address On Port 0/1.
b) Configure The IP Address On All Ports.
c) Configure The IP Address On The Management VLAN.
d) Configure The IP Address On All Vlans.
e) You Cannot Configure An IP Address On A Switch.
Answer: c
20. WHERE IS FRAME TAGGING NECESSARY TO IDENTIFY VLAN MEMBERSHIP?
a) Between The Source Workstation And The Nearest Switch.
b) Between Switches If A Link Carries Frames Belonging To More Than One VLAN.
c) Between Switches If A Link Carries Frames Belonging To Only One VLAN.
d) Between The Switch And The Destination Workstation.
Answer: b
21. WHICH STATEMENTS ARE TRUE OF IEEE 802.1Q FRAME TAGGING? (CHOOSE TWO)?
a) It Is A Cisco Proprietary Encapsulation Protocol.
b) It Inserts A VLAN Identifier And Other Fields Into The Frame Header.
c) It Encapsulates The Frame With An Additional Header.
d) It Is Now The Preferred Method For Identifying VLAN Traffic Between Switches.
e) It Used To Be The Most Common Method For Identifying VLAN Traffic Between Switches, But It Is Not In Common Use Any More.
Answer: b And d
22. WHERE IS FRAME TAGGING ADDED TO THE FRAME?
a) At The Source Host Workstation.
b) At The Destination Host Workstation.
c) At A Switch, Before The Frame Is Placed On A Trunk Connection.
d) At A Switch, After The Frame Is Received From A Trunk Connection.
Answer: c
23. WHERE IS FRAME TAGGING REMOVED FROM THE FRAME?
a) At The Source Host Workstation.
b) At The Destination Host Workstation.
c) At A Switch, Before The Frame Is Placed On A Trunk Connection.
d) At A Switch, After The Frame Is Received From A Trunk Connection.
Answer: d
24. WHICH COMMANDS WOULD YOU USE IN ORDER TO CREATE A VLAN NUMBER 4, CALLED MARKETING?
a) Switch# vlan 4
Switch(vlan)#name Marketing
b) Switch(config)# vlan 4
Switch(config-vlan)#name Marketing
c) Switch(config)#vlan access
Switch(config)#vlan 4 name Marketing
d) Switch(vlan)#vlan 4
Switch(vlan)#name Marketing
e) Switch(config)#vlan 4 Marketing
Answer: b
25. WHICH COMMANDS WOULD YOU USE IN ORDER TO ASSIGN THE FAST ETHERNET PORT 0/7 TO VLAN 4? (CHOOSE THREE)
a) Switch(Vlan)# Interface Fastethernet 0/7
b) Switch(Config)#Interface Fastethernet 0/7
c) Switch(Config-If)#Switchport Mode Access
d) Switch(Vlan-If)#Switchport Access Vlan 4
e) Switch(Config-If)#Switchport Access Vlan 4
f) Switch(Config-If)#Switchport Vlan 4
g) Switch(Config)#Interface Fastethernet 0/7 Vlan 4
h) Switch(Config-If)#Switchport Mode Access Vlan 4
Answer: b,c,e
26. PORTS 0/7, 0/8 AND 0/9 ALL BELONG TO VLAN 4. YOU GIVE THE COMMANDS
Switch(Config)#Interface Fastethernet 0/9
Switch(Config-If)# No Switchport Access VLAN 4
WHICH OF THE FOLLOWING STATEMENTS IS TRUE?
a) VLAN 4 Has Been Deleted.
b) All Three Ports Have Been Removed From VLAN 4.
c) Port 0/9 Is Now Inactive And Needs To Be Assigned To A New VLAN.
d) Port 0/9 Is Reassigned To VLAN 1.
Answer: d
27. PORTS 0/7, 0/8 AND 0/9 ALL BELONG TO VLAN 4. YOU GIVE THE COMMAND
Switch(Config)# No Vlan 4
WHICH OF THE FOLLOWING STATEMENTS ARE TRUE? (CHOOSE 2)
a) VLAN 4 Has Been Deleted.
b) All Three Ports Have Been Assigned To VLAN 1.
c) VLAN 4 Still Exists But The Ports Are No Longer Assigned To It.
d) All Three Ports Are Inactive And Not Assigned To Any VLAN.
e) All Three Ports Will Be Reassigned To VLAN 1 When The Switch Is Reset.
Answer: a And d
28. WHICH COMMAND WOULD YOU GIVE TO VIEW THE CONTENTS OF THE VLAN DATABASE?
a) Switch#Show Vlan
b) Switch#Show Vlan Database
c) Switch#(Vlan)Show Vlan
d) Switch#(Vlan)Show Vlan Database
e) Switch#Show Database Vlan
Answer: a
29. IF YOU DO NOT SPECIFY WHICH VLANS ARE ALLOWED ON A TRUNK LINK, WHAT WILL HAPPEN?
a) No Vlans Can Send Traffic Over The Link.
b) Only VLAN 1 Can Send Traffic Over The Link.
c) Only The Management VLAN Can Send Traffic Over The Link.
d) All Vlans Can Send Traffic Over The Link.
Answer: d
30. WHICH IS TRUE ABOUT VLAN INFORMATION?
a) You Should Save The Running Configuration So That VLAN Information Is Held In The Startup Configuration.
b) VLAN Information Is Held In The VLAN Database In Flash Memory.
c) You Can Remove VLAN Information By Giving The Erase Start Command And Reloading.
d) VLAN Information Is Not Saved, But Is Re-Learned From Neighbouring Switches On Start-Up By Using CDP.
Answer: b
31. IEEE 802.1q AND ISL ARE:
a) Different Encapsulation Methods For Tagging Frames On Trunk Links.
b) Both Supported On All Cisco Catalyst Switches.
c) Different Methods Of Assigning Devices To Vlans.
d) Different Methods Of Sharing VLAN Information Between Switches.
Answer: a
32. A SWITCH PORT HAS BEEN CONFIGURED AS FOLLOWS:
SW1(Config)#Int Fa 0/12
SW1(Config-If)#Mls Qos Trust Cos
SW1(Config-If)#Switchport Voice Vlan 150
SW1(Config-If)#Switchport Mode Access
SW1(Config-If)#Switchport Access Vlan 5
SW1(Config-If)#End
WHICH IS TRUE?
a) There Is A Conflict Because The Port Has Been Configured On Two Vlans.
b) The Port Is On VLAN 5 Only, Because The Later Configuration Replaces The Earlier Configuration.
c) The Port Can Handle Both Voice And Data Traffic.
d) The Port Will Give Priority To Traffic On VLAN 5.
Answer: c
33. WHAT IS THE PROBLEM WITH THE NETWORK IN THE ABOVE DIAGRAM?
a) It Is Not Possible For A Router To Have Four Fastethernet Ports.
b) The Vlans Will Not Be Able To Communicate With Each Other.
c) The Router Is Not Needed Because These Vlans Can Communicate Through The Switch.
d) This Design Will Not Scale Well If More Vlans Are Added.
Answer: d
34. Another VLAN Is Added To The Network Shown Above, But The Router Does Not Have A Spare Fastethernet Port. What Would Be The Most Economical Solution?
a) Buy An Extra Module For The Router To Provide More Fastethernet Ports.
b) Connect An Extra Router, Link The Two Routers Together And Enable A Routing Protocol Between Them.
c) Configure A Trunk Link On The Switch And Subinterfaces On One Of The Router Ports.
d) Use A Cheap Hub To Connect All The Vlans To The Same Router Interface.
Answer: c
35. A TRUNK LINK BETWEEN A ROUTER AND A SWITCH IS CARRYING TRAFFIC FOR SIX VLANS. WHAT IS A POTENTIAL PROBLEM?
a) The Vlans Are Sharing The Link’s Bandwidth And This Could Create A Bottleneck.
b) The Volume Of VTP Traffic On The Link Is Likely To Have An Adverse Effect On The Network’s Performance.
c) The Traffic For The Different Vlans Is Likely To Be Confused As All The Traffic Goes Through The Same Physical Router Interface.
d) The Maximum Number Of Subinterfaces That Can Be Configured On A Router Port Is Five.
Answer: a
36. A SWITCH IS CONFIGURED AS FOLLOWS:
SW(config)#int f0/1
SW(config-if)#switchport mode access
SW(config-if)#switchport access VLAN 3
SW(config-if)#description link to router f0/0
SW(config)#int f0/2
SW(config-if)#switchport mode access
SW(config-if)#switchport access VLAN 3
SW(config-if)#description link to router f0/1
SW(config)#int f0/3
SW(config-if)#switchport mode access
SW(config-if)#switchport access VLAN 3
SW(config-if)#description link to PC A
SW(config)#int f0/4
SW(config-if)#switchport mode access
SW(config-if)#switchport access VLAN 4
SW(config-if)#Description link to PC B
WHY IS PC A UNABLE TO PING PC B?
a) There Needs To Be A Trunk Link To The Router In Order For Vlans To Communicate With Each Other.
b) The No Shutdown Command Has Not Been Given On The Switch Interfaces.
c) The Router Will Not Handle Traffic To Or From VLAN 4.
d) Interface F0/1 On The Switch Should Be Connected To Interface F0/1 On The Router.
Answer: c
37. A ROUTER IS TO BE ADDED TO THE CONFIGURATION SHOWN IN THE DIAGRAM ABOVE. THIS WILL ALLOW COMMUNICATION BETWEEN THE DIFFERENT VLANS. HOW MANY FAST ETHERNET PORTS WILL THE ROUTER NEED?
a) None, Serial Ports Must Be Used.
b) One, Since Trunking Can Be Used.
c) Two, One Connecting To Each Switch.
d) Three, One For Each VLAN.
e) Six, One For Each VLAN On Each Switch.
Answer: b
38. HOW MANY IP ADDRESSES MUST BE CONFIGURED ON THE ROUTER MENTIONED IN THE PREVIOUS QUESTION?
a) None, Because Vlans Operate At Layer Two.
b) One, Because Only One Physical Ports Is Needed.
c) Two, One For Each Switch.
d) Three, One For Each VLAN.
e) Six, One For Each VLAN On Each Switch.
Answer: d
39. SHOWN IN THE DIAGRAM ABOVE, SWITCHPORT 0/4 IS ON VLAN2, PORT 0/6 IS ON VLAN3, PORT 0/8 IS ON VLAN4.
PART OF THE ROUTER CONFIGURATION IS AS FOLLOWS:
Router(Config)#Interface Fastethernet 0/1.2
Router(Config-Subif)#Encapsulation Dot1q 2
Router(Config-Subif)#IP Address 192.168.1.0 255.255.255.240
Router(Config)#Interface Fastethernet 0/1.3
Router(Config-Subif)#Encapsulation Dot1q 3
Router(Config-Subif)#IP Address 192.168.1.33 255.255.255.240
Router(Config-Subif)# Interface Fastethernet 0/1.4
Router(Config-Subif)# Encapsulation Dot1q 4
Router(Config-Subif)#IP Address 192.168.1.49 255.255.255.240
WHICH OF THE FOLLOWING HOST IP ADDRESSES ARE SUITABLE? (CHOOSE 2)
a) Host A, 192.168.1.20
b) Host A, 192.168.1.32
c) Host B, 192.168.1.46
d) Host B, 192.168.1.47
e) Host C, 192.168.1.44
f) Host C, 192.168.1.60
Answer: f
40. TOPOLOGY AND CONFIGURATION ARE THE SAME AS IN THE PREVIOUS QUESTION. HOST IP ADDRESSES ARE SET AS FOLLOWS:
Host A, 192.168.1.13
Host B, 192.168.1.50
Host C, 192.168.1.58
WHICH STATEMENTS ARE TRUE? (CHOOSE ALL THAT APPLY)
a) Host A Can Receive Messages From Host B
b) Host A Can Receive Messages From Host C
c) Host B Can Receive Messages From Host A
d) Host C Can Receive Messages From Host A
Answer: b And d
41. A ROUTER-ON-A-STICK IS CONFIGURED AS FOLLOWS:
R(Config)#Interface F0/1.2
R(Config-Subif)#Encapsulation Dot1q 20
R(Config-Subif)#IP Add 172.18.0.1 255.255.255.128
R(Config-Subif)#Interface F0/1.3
R(Config-Subif)#Encapsulation Dot1q 30
R(Config-Subif)#IP Add 172.18.0.161 255.255.255.224
R(Config-Subif)#Interface F0/1.4 R(Config-Subif)#Encapsulation Dot1q 40
R(Config-Subif)#IP Add 172.18.0.193 255.255.255.224
R(Config-Subif)# Interface F0/1
R(Config-If)#No Shutdown
THE ROUTER RECEIVES A FRAME ON PHYSICAL INTERFACE F0/1. THE DESTINATION IP ADDRESS IS 172.18.0.120. WHAT WILL THE ROUTER DO?
a) Drop The Frame Because The IP Address Is Not On A Known Network.
b) Send The Frame Out Of Interface F0/2.
c) Send The Frame Out Of Interface F0/1.2 Tagged For VLAN 2.
d) Send The Frame Out Of Interface F0/1.2 Tagged For VLAN 20.
Answer: d
41. WHICH IS TRUE OF INTER-VLAN ROUTING USING “ROUTER-ON-A-STICK”?
a) Not Every Router Is Able To Create Subinterfaces For Vlans. It Depends On The IOS Features.
b) It Is Possible If The Switch Uses IEE802.1Q Tagging, But Not If The Switch Uses ISL.
c) The Router Has To Be Running A Routing Protocol That Supports VLSM.
d) The Configuration Is Simpler Than If Separate Physical Interfaces Are Used, But The Cabling Is More Complicated.
Answer: a
42. HOW ARE DEFAULT GATEWAYS CONFIGURED FOR INTER-VLAN ROUTING WHEN “ROUTER-ON-A-STICK” IS USED?
a) All Pcs Attached To The Switch Will Share The Same Default Gateway Since There Is Only One Physical Connection To The Router.
b) PCs On Different VLans Must Be Configured With Different Default Gateways.
c) Pcs Must Be Configured With The Same Default Gateway As The Switch.
d) The Switch Default Gateway Is The IP Address Of The Physical Interface On The Router.
Answer: b
43. WHAT IS TRUE ABOUT MAC ADDRESSES WHEN “ROUTER-ON-A-STICK” IS USED FOR INTER-VLAN ROUTING?
a) Each Subinterface On The Router Has Its Own MAC Address.
b) Each Default Gateway At Layer 3 Is Linked With A Different MAC Address At Layer 2.
c) Each Physical Ethernet Interface On The Router Has One MAC Address.
d) The MAC Address Of The Router Interface Is Not Used When The Interface Is Configured For Trunking.
Answer: c
CONCLUSION:
The Goal Of This Article Is To Give An Easy Way To Understand The “Create VLAN Step By Step Configuration Example" And Also We Hope This Guide Will Help Every Beginner Who Are Going To Start Cisco Lab Practice Without Any Doubts. Some Topics That You Might Want To Pursue On Your Own That We Did Not Cover In This Article Are Listed Here!Hands - On Experience Is An Invaluable Part Of Preparing For The Lab Exam And Never Pass Up An Opportunity To Configure Or Troubleshoot A Router ( If You Have Access To Lab Facilities, Take Full Advantage Of Them) There Is No Replacement For The Experience You Can Gain From Working In A Lab, Where You Can Configure Whatever You Want To Configure And Introduce Whatever Problems You Want To Introduce, Without Risk Of Disrupting A Production Network. Thank You And Best Of Luck
This Article Written Author By: Premakumar Thevathasan - CCNA, CCNP, MCSE, MCSA, MCSA - MSG, CIW Security Analyst, CompTIA Certified A+ And Etc.
WARNING AND DISCLAIMER:
Routers Direct And Control Much Of The Data Flowing Across Computer Networks. This Guide Provides Technical Guidance Intended To Help All Network Students, Network Administrators And Security Officers Improve Of Their Demonstrated Ability To Achieve Specific objectives Within Set Timeframes.This Document Carries No Explicit Or Implied Warranty. Nor Is There Any Guarantee That The Information Contained In This Document Is Accurate. Every Effort Has Been Made To Make All Articles As Complete And As Accurate As Possible, But No Warranty Or Fitness Is Implied.
It Is Offered In The Hopes Of Helping Others, But You Use It At Your Own Risk. The Author Will Not Be Liable For Any Special, Incidental, Consequential Or Indirect Any Damages Due To Loss Of Data Or Any Other Reason That Occur As A Result Of Using This Document. But No Warranty Or Fitness Is Implied. The Information Provided Is On An "As Is" Basic. All Use Is Completely At Your Own Risk.
Home Page Of - > The School Of Cisco Networking (SCN)
Page Of - > SCN InF4 TECH
Contact Details / About Us Page
To Send Email
Window Minimize /
Window Maximize












1 comment:
Need to add VLAN wise traffic stop via Route ACL or VLAN ACL,,,pls expalin Router base ACL with example,,its very worth to knowledgeable for Us
Post a Comment